How To: Effectively Manage Your Client Passwords
BY IT GLUE | June 21, 2016
When it comes to client credential management, there are some essentials we all need:
- secure storage
- to be managed centrally
- to be quickly accessible
If your password management system falls short in any of these three areas, then you are already wasting time each day and crucially putting your clients’ data at risk.
These are the things that you should consider in each of these areas:
Secure
- complexity rules for passwords are designed and enforced
- encrypted storage is as “un-hackable” as you can make it
- access control is granular and configurable
Managed
- credentials are changed on a regular basis (e.g. every 90 days) and triggered by events (e.g. key team member leaves your organization)
- you have a separate password for every client, every system and every access level
- auditing is in place to show who created, edited, viewed, or deleted a credential
- policies are in place for safe communication of passwords (e.g. NEVER emailed, printed or written on a post-it, never shared with unauthorized individuals)
Accessible
- your team can get to the passwords they need instantly to do their job from any location, using any device, be it mobile or desktop
Give yourself a quick audit on how your team currently stands on “secure, managed and accessible”. Be brutally honest. I guarantee every one of your team places a high value on these three areas, and everyone agrees with the theory. But what is ACTUALLY happening daily?
This brings us to one crucial fourth item of credential management: context.
You can have the most secure, well managed, and accessible password management system on the planet, but if you don’t know which password to use for which task, you could be spending a lot of unnecessary time searching for information and frustratingly entering incorrect passwords into logon screens.
Context
- ensure your credentials have a consistent naming standard where possible
- create meaningful folders/groups for ‘client specific’ and ‘central’ credentials
- refer to passwords specifically in procedures, reference documents and configurations
If you are using IT Glue™, use related items liberally and constantly. When you enter a credential (e.g. Active Directory password), consider every single system that is authenticated by that password, and link it. New starter procedures, application accounts, wireless auth, VPN, workstation builds, federation and more.
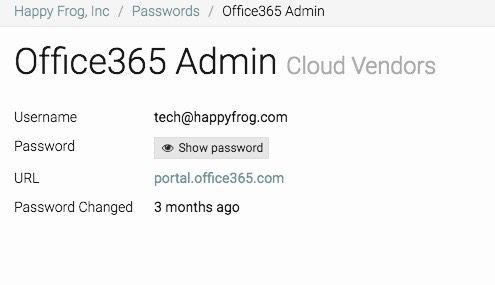
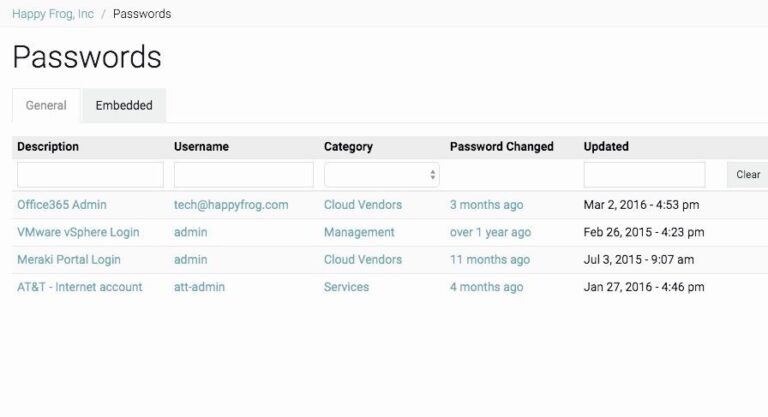
Above: Examples of your password management in IT Glue
If your credential management technology and policies can be classed as secure, managed, accessible and contextual, this is an excellent indicator of operational maturity. You are minimizing wasted time and maximizing trust. Your clients have high expectations that you have spent significant energy investing in this vital area of their business, and yours.
| How to Home | ← How to Get Your Team Using MFA | How to Work with Domains and SSL Certificates → |